Search Results for:
Loading...

SECURITY LOOPHOLES can cause you millions of dollars! We make sure that such things does not happen
we can help you in
- Boosting defence system
- Track vulnerabilities
- Prioritise risk
- Prevent infiltration
- Helps you in standard and regulatory compliance
Wish to know about the companies that trusted us?






WHAT IS PENETRATION TESTING?
It’s a tedious task of finding out potential loopholes in your software system by simulating an attack from outside. Since the test takes place in the perspective of a potential hacker even the minute vulnerability can be fished out to make the website/app hack proof.
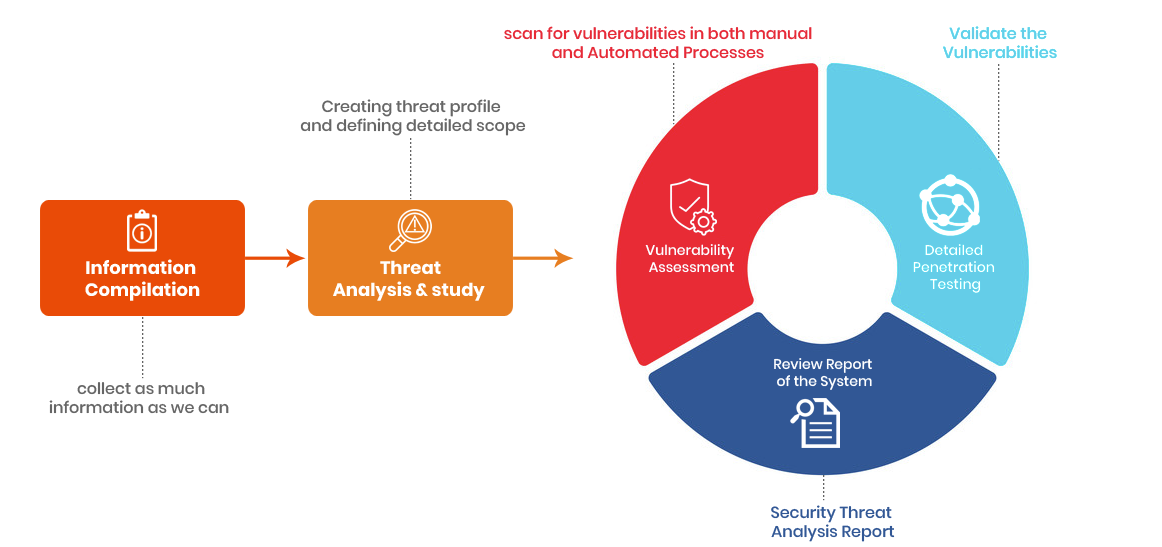
OUR SECURITY TESTING APPROACH
WHY DO YOU NEED ATTACK SIMULATION?
- Helps in finding out that the money that you have been investing in security is worth it
- Finds out the system deployed for security is mature enough
- Complete information gathering to find out what’s that one or multiple weak spots
- Can save you millions of dollars
- Will be able to find out all the desperate measures that a hacker would use
THE RANGE OF PENETRATION TESTING SERVICES WE OFFER:
- Internal and External Network Penetration Testing
- Network Security Architecture Review
- Wireless Network Security Assessment
- Security Configuration Review
BENEFITS OF OUR PENETRATION TESTING SERVICE
- Helps you in evaluating your tech assets
- Assurance for effective security implementation
- Breach detection of both internal and external systems
- Simulation of most dreaded attacks
- Risk Helps in developing a deter risk management policy
- Helps you in meeting compliance and regulatory standards such as IPAA, PCI, DSS, NIST etc
WHAT WILL WE DELIVER AFTER THE TEST?
- Brief about our tests, achievements and findings
- List of vulnerabilities, their classification and threat level
- Changes we induced in the system for mending it our way
- Devices and systems we used and protocols we followed
- Sudden and far-sighted recommendations.

FAQ
- 1. How does penetration testing work?
Estimation of over-all scope and risk assessment will be calculated in the first itself. The complexity of the system will also be defined. Basically, we gather as much information as we can analyze it deeply, and come up with a solution.
- 2. What can I expect from the pen-testing process?
- It’s a highly disciplined process and requires detail to the attention which we are indebted to do
- The documentation will be in detail and extensive
- All the stake-holders of the project will be kept well informed throughout the project
- Our approach towards every project will be customized according to the nature of the environment.
- 3. How do you define the scope for penetration testing of my requirement?
- Costing will be dependant on factors like,
- Nature of your business
- Geographic variances
- Structure of the organization
- Custodianship of data
- Network segmentation
- Environment redundancy etc.
- 4. How much time do you need to perform the tests?
- 4-6 weeks is the average time we take. However, the size of the environment obviously will have a huge impact on the duration of the test
- 5. What’s it that you test while performing the process?
- System-level – The environment in which the application thrives
Technology – Will have a deep look at the capability of security features and systems
Logic – functionalities of the security system and internal processes
- 6. Do you offer a CVSS(“The Common Vulnerability Scoring System (CVSS) score?
- Yes, we do!
- 7. Can you automate a pen test and make sure that the process is much faster?
- If it’s just vulnerability scanning yes it’s possible. However, complex programs require custom and manual and automation.
- 8. I have availed hosting service should that be tested too?
- Usually hosting environment is heavily guarded centrally. However, to be on the safe side you can request the hosting provider that the tests that are going to take place will be extended to them.
Our Blog
Have a look at our insights on Testing industry

Selenium vs Puppeteer vs Chai Mocha
The software life cycle has undergone drastic changes in the…

Top 50 Must Read Jmeter Interview Questions
To be able to answer the questions about Jmeter Interview…

Jmeter Tutorial: Learn about the tool in a jiffy!
Jmeter Tutorial blog by us will help you in learning…
Send us your requirement. Our representative will get back to you within no time

AngularJS Testing Tutorial - Cypress, Karma and Protractor
AngularJS testing using selenium is not a good approach. Due…
Protractor vs Selenium: What are the major differences?
Protractor vs selenium who will win? Both the test automation…

15 Top Selenium WebDriver Commands For Test Automation
The use of selenium webdriver helps in testing every aspect…
Mobile Atomation testing
Overview
Services
Industries
Contact Us
- Kalas road, Vishrantwadi,
Pune, Maharashtra-411015 - 65 Broadway Suite 1101,
New York NY 10006 - sales@testreveal.com
- +91 8113865000

Copyright © 2025 | Digital Marketing by Jointviews