Search Results for:
Loading...

Get rid of bugs in
your coding through proper audit
We can assure
- Quick testing
- Standards and compliance check
- Weekly or daily report
- Weekly or daily reportQuick testing
- Weekly or daily report
Services we offer
Error assessment
Vulnerability assessment
Access assessment
Compliance and standard check
Detailed audit report
Integrated security library verification
Source code assessment of both existing one and new ones
Our Clients















































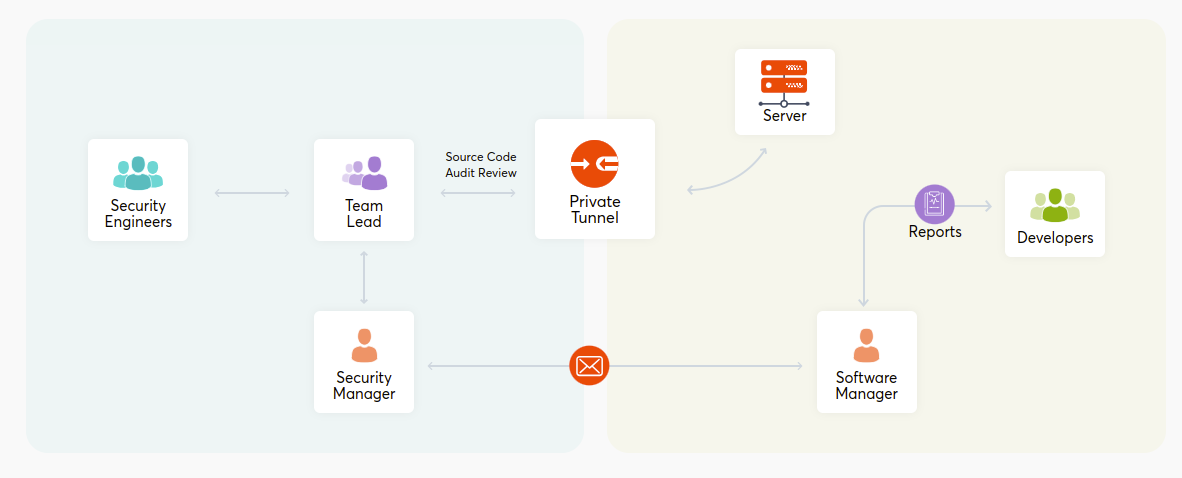
Our unique approach in source code audit/testing
- Test case driven approach developed by experts who has impeccable testing knowledge
- Tool selection based on structure of the software so that unmatchable efficiency can be guaranteed
- All the security loop-holes will be revealed with our scenario based testing
- Standards and compliance check to make sure that quality is maintained
- Perfect code mapping, application work flow validation and business logic evaluation
Our simple yet perfect working procedure
Wish to talk to us?
- info@testbytes.net
- Sales: +1 929 552 0053
- HR: +91 8113 862 000
Why do you need to audit the source code of your software?
At this juncture of time none can turn a blind eye towards security. Imagine your software has been attacked? Will there be a comeback? If there is, how will the devastation affect your company? Once the reputation is lost it’s gone forever. What about that huge sum that you need to churn up to rectify the damage that’s been done
What would be the possible solution here?
You need to put out there something that’s near to flawless. All the possible issues have to be rectified. For that, what else to rely on than source code audit?

Why do we recommend automated source code testing?
- Faster than you can imagine
- SDLC will also become faster
- Flaws and vulnerability detection will be more accurate
- Better usage of tools
- Continuous testing can be guaranteed
Why us
- Errors can be reduced to a considerable amount before deployment
- Security loop holes can be found out and rectified
- Tailored approach in accordance with the nature and build of the software
- Testing will be performed by our best
- Defensive mechanism of your system including risk management, internal structure will be audited
- Once the audit is completed, you will get a final report that has detailed information about the all the tests and its results
FAQ
- 1. Do you have programmers to evaluate the code?
Yes we do! we have testers who have impeccable knowledge in leading programming languages and libraries that’s being used at present.
- 2. Who makes decision in your company?
Our CEO and business head will be responsible for that
- 3. Can you tell us more about yourself?
Sure, why not? please click here to read about us extensively
- 4. What's your typical response time to email and messages
We are prompt in communication. We try to reach you as early as possible
- 5. Can you start working on our project as quickly as possible?
Why not? once the initial formalities are carried over, we will get into the project
- 6. How can you keep me updated ?
Regular communication by slack, JIRA and skype will be carried over. Daily report and weekly report will also be provided upon request
Our Blog
Have a look at our insights on Testing industry

An Analysis of the Effects of the Agile Model in Software Testing
Software professionals are under pressure to d

Web Application Testing Manually (Step by Step A Complete Guide)
Web applications are a subset of application s

Unit Testing Best Practices: 11 Effective Tricks
Unit tests are great! I mean look at the
Send us your requirement. Our representative will get back to you within no time

Agile VS DevOps: Difference between Agile and DevOps
Agile vs DevOps which is better? Agile, Scrum,
Automation Testing Tutorial For Beginners
Automation testing not only relieves testers o

https://www.testbytes.net/blog/ux-testing-practices/
We make inquiries. We take notes. We get the h
Mobile Atomation testing
Overview
Services
Industries
Contact Us
- Kalas road, Vishrantwadi,
Pune, Maharashtra-411015 - 65 Broadway Suite 1101,
New York NY 10006 - sales@testreveal.com
- +91 8113865000

Copyright © 2025 | Digital Marketing by Jointviews