Search Results for:
Loading...
Is your software safe from cyber attacks & data loss/leakage?
Find out with information security testing
- Reduce security risks
- Improve data security
- Reduce network downtime costs
- Win trust of your customers
- Experience improved quality

Our top quality application testing services will help you
- Run security checks for mobile and web applications, APIs, cloud and desktop applications
- Know if your data remains encrypted and protected under any circumstances
- Add security layers for your application keeping functionality in-tact
- Get a detailed report of all the security loopholes in your software
- Check whether your software comply to regulations and standards
Prevent Breaches, Recovery is expensive
Information security testing is crucial as any type of attack can become deadly for your company through data loss or leakage, privacy breach etc. The integrity, confidentiality and authenticity of your company can end up getting questioned by users.
Our security testers are skilled, experienced and is professionally certified to carry out any form of security testing. With the help of ethical hackers, we trace out all the vulnerabilities in your system so that your developers can seal them and make your software hackproof.

Information Security Testing Services We Offer
At Testbytes, we provide comprehensive information security testing services designed to find all the bugs that’s affecting or going to affect your software. These are listed below
- Standards based security testing (OWASP top 10, SANS Top 25, OSSTM, NIST 800-15 etc.)
- Threat modelling
- Vulnerability assessment
- Penetration testing
- Network testing
- Authentication testing
- Authorisation testing
- Web services testing
- Data validation testing
- Denial of service testing
- Ajax Testing
- Session management testing
- Configuration testing
- Code review
- Compliance testing
- Security consultation
Check out our exclusive playlist for Security testing
For a better understanding of your requirement, can you please download this sheet, fill it up and send it to us?
Some cyber threats we can help prevent
- Phishing attacks
- Drive-by attack
- Cross Site Scripting
- Password attack
- Birthday attack
- MITM attacks
- Ransomware attack
- SQL Injection
- DDoS attack
- Network interception
- Brute-force attack
- Iot attack

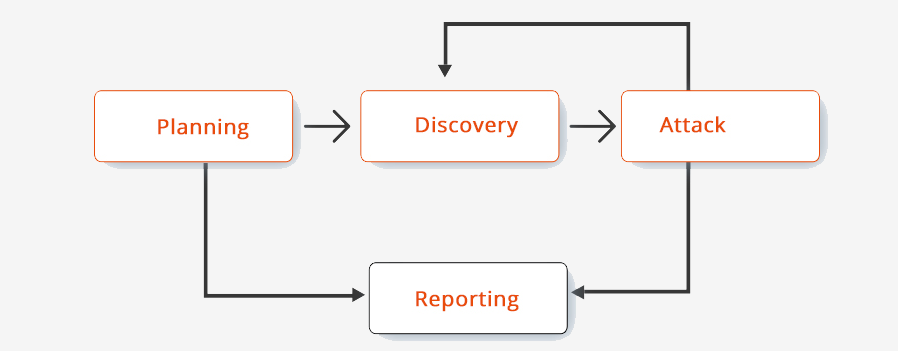
Our Security Testing Process

Discovery and documentation
Once we get hold of the software, we do a thorough study to understand to understand user profiles, functionality, workflow and coding.

Profiling
core security mechanism in the application, user entry points will be found out along with flow of the data

Scanning
combination of automated testing and manual testing will be performed to trace out the all the issues. Those security issues missed by automation testing will not escape after manual testing

Vulnerability exploitation
Combinatorial testing mentioned above will be used to find all the vulnerabilities of the software

Reporting
All the traced out issues will be reported in detail and will be send to clients
When and how
often you should perform security testing?
Remember! They are waiting for an opportunity. Do not give it to them. The loss can be devastating.Performing security testing on constant intervals will reveal how strong your software is. However, there are certain times when testing has to be mandatory which includes,
- Before deployment of software
- New network is added to the main system/ or the main network is integrated to the central system
- Security patches are added to the program
- End user policy addition or updation

Our Approach
What makes us different than other Penetration/security testing companies?
- Holistic approach
- Better protection for your business information
- Dedicated team at your service including testers/architects and analysts
- Hire any number of testers based on your requirement
- Expertise in major technologies and good knowledge about regulatory compliance
- Elaborate reporting
- Risk analysis will be performed and mitigation methodologies will be devised
- Possession of wide range of open-source and licensed tools for wide range of security testing
- Our testers are armed with the necessary professional certifications
Mobile app testing tools – Automation tools
Appium

Robotium

Calabash
Industries we have worked for

Education

Automotive

Enterprise

Healthcare
IoT

Productivity

Games

Entertainment
Logistics

E-Commerce
Game Testing
FAQ
- 1. Automated vulnerability assessment and pen testing how do they differ?
Automated vulnerability assessment as the name suggests is an automated test where certain tools are used to assess the common vulnerabilities of a system (network included). Since the process is automated, it requires less time and is cost-efficient. Pen testing on the other hand tests the system as a whole thoroughly, in short, a comprehensive analysis of the security posture of a company is possible. Pen testing is a combination of both manual as well as a software process. The process can act as a potential hacker and who would try to break into your system by any means so that issues about your system or company cybersecurity can be revealed at the earliest.
- 2. Do you offer certificates for the test you have conducted?
At present we don’t! As far as we know, none is offering such. What we can assure here is experienced and clever testers who have state-of-the-art resources at their disposal to conduct security testing with efficiency and within the proposed deadline. Al the tests will be documented and the findings will be reported on daily, weekly or monthly basis based on the requirement.
- 3. What’s the end goal of security testing that you do?
It’s defined by the scope. However, we believe that the testing that we do can evaluate the security measures used in software or a company is enough to protect itself from a harmful attack.
- 4. What kind of penetration testing do you do?
- Internal Network Penetration Test
- Internal Wireless Penetration Test
- Remediation Verification
- Remote Social Engineering
- 5. How much does security testing cost?
- A lot of factors that go into deciding cost; however, we have created a cost calculator to increase transparency and to reduce the hassle. Click here!
You can also contact us directly if you need a custom quote. Click here!
Overview
Services
Industries
Contact Us
- Kalas road, Vishrantwadi,
Pune, Maharashtra-411015 - 65 Broadway Suite 1101,
New York NY 10006 - sales@testreveal.com
- +91 8113865000

Copyright © 2025 | Digital Marketing by Jointviews